What is tor Browser? How to set up and use it

TOR is a browser configured in a certain way, which guarantees anonymity of Internet use. Incognito mode is achieved by encrypting traffic and routing it to servers. Using the browser allows you to hide the user’s identity and protect web connections from various types of surveillance. An additional option of TOR is to bypass Internet blocking. Let’s familiarize ourselves with the capabilities and features of the browser.
TOR – what it is, advantages and disadvantages of the technology
TOR is a tandem of a modern version of Mozilla Firefox and software with an emphasis on privacy. The program is free, allows you to effectively bypass censorship in the network. The browser network consists of many servers scattered around the world, which are managed by volunteers.
Anonymity is ensured by connecting to three relays, each of which is encrypted. As a result, it becomes impossible to calculate the path from the movement of information from the recipient to the sender.
When using TOR, a different IP address is used, which often belongs to another country. In this case, the IP address is hidden from the sites visited by the user. An additional security measure is the encryption of visited sites from unauthorized persons who can intercept the movement of traffic.

This reduces the risk of online snooping to zero. Also TOR allows you to bypass Internet filters. The user becomes available sites and resources that were previously inaccessible due to blocking within the country.
Advantages of using it:
- protection from surveillance that could pose a privacy threat;
- absence of built-in systems for tracking the user;
- simplicity of the system, even an inexperienced user can easily handle the program;
- technology does not capitalize on the user’s data;
- the browser is recommended by many security experts;
- dynamism of the program – it can be run from any type of media, including portable media;
- the browser blocks all network features that could jeopardize security.
Using TOR is not without disadvantages. The main of which is considered a low download speed. At the same time, the user is limited in the ability to use all the functions of some of the resources.
The process of downloading and installation
To begin with, you need to go to the official site of Tor Browser – https://www.torproject.org. Click the “download” button, after which you will be presented with a table of different versions. Choose the appropriate one and continue downloading. If the site is inaccessible for you, you can send a request email to [email protected]. Specify the required version, after which you will receive a download link that will not be blocked.
To use the program Tor does not require a standard installation procedure. It is enough just to unzip the browser on your PC and run it from there. If you still wish to install Tor, follow these steps:
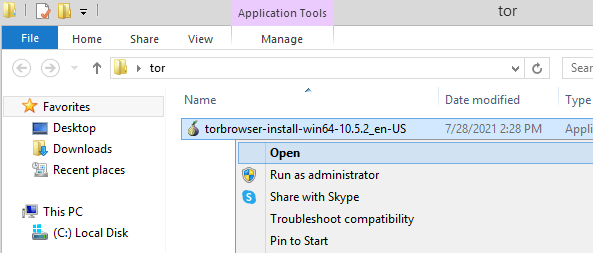
- go to the “downloads” folder;
- open the file, select the desired installation language;
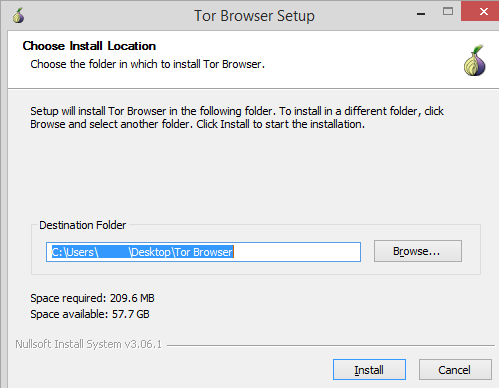
- select the installation folder of the program;
- click “ok” and “ready”.
The installation is complete. A shortcut will appear on the desktop.
How to configure TOR for personal work?
During the first startup, the program will ask the type of connection to be selected. TOR offers 2 types of connection:
- direct connection – should be chosen when you have unlimited access to the network, in those countries where the browser is not legally banned, the use of the program is not monitored by the relevant services;
- limited connection – should be selected when access to the network is limited, for countries where the use of the browser is blocked or prohibited.
In the first case, you need to launch the program and select the “connection” section. After that the use of the browser will be available.
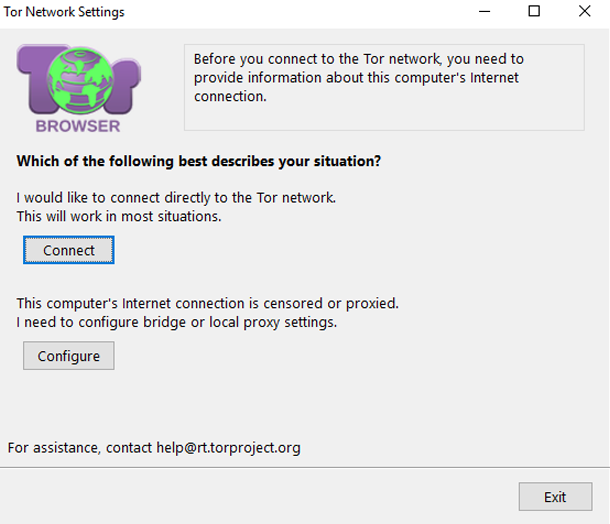
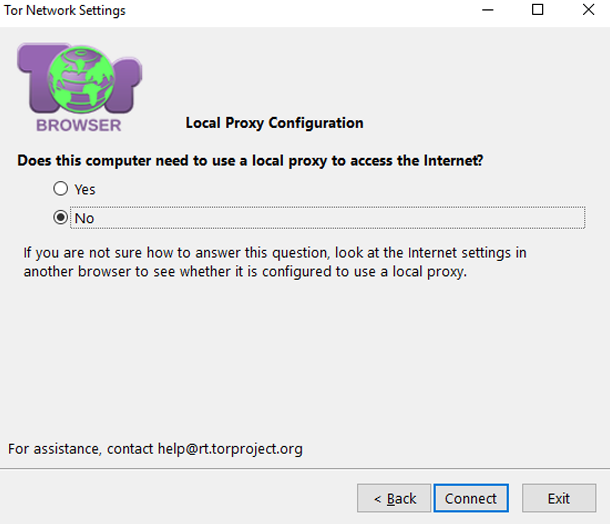
In the second case, it is necessary to additionally encrypt TOR bridges. Select “restricted access” and press the “settings” key. Now go to the configuration of bridges. In the window that opens, select the section “connect to predefined bridges”. Next, the program will ask you whether you need a proxy to provide access to the network. Select the “no” option. Then click on “connect”.
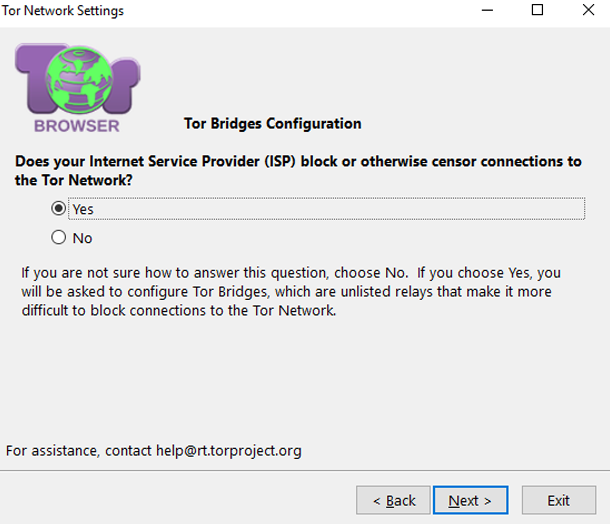
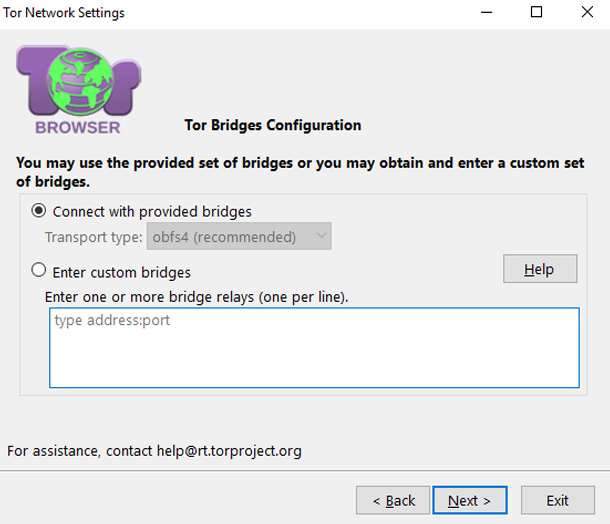
The alternative is to select bridges independently. This method is rarely used, so the probability that you will be blocked is minimal. The user needs to go to the Tor Project website and request the addresses of existing bridges. Then you just need to follow the instructions.
After receiving the information, you can personally enter the addresses of bridges in the settings and use the browser.
Features of use
Using TOR is very simple. It is a classic browser with one important feature – privacy mode. You can also visit resources and sites of interest without the threat of surveillance. However, questions may arise if you, for example, go to a country where the use of TOR is prohibited. In this case, follow the steps:
- go to the browser menu;
- select connection settings;
- change the method of connection to the Internet (see the section above about limited connection);
- after completing the settings, click “ok” and restart the program.
When using the technology, it is worth remembering that online activity will be protected only within the TOR browser. The program does not protect other online activities of the user. When you visit TOR, your transaction history is only available when you are using the program. As soon as you exit it, the history will be automatically cleared without saving it to your PC hard disk.
To check if the browser is active, you should visit the developer’s website – https://check.torproject.org/. When using the program, you can create new identities. This can be done in the settings menu. When you do this, the browser will select new retranslators that will provide anonymity.
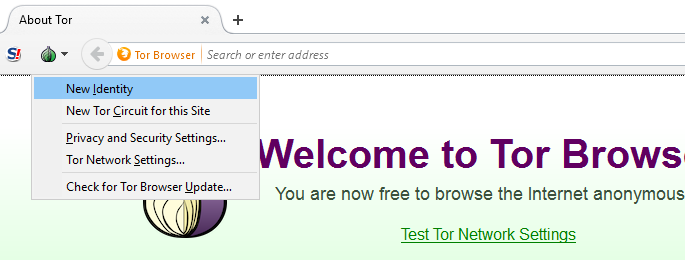
When using the web, it will look as if you have logged on to the internet under a different IP address. An additional security measure is the NoScript option. It is not active by default, but it can be enabled.
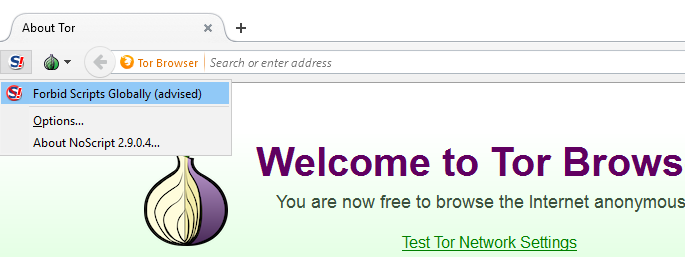
Its activity is aimed at protecting the user from data leakage through scripts and protection from potentially malicious sites. To activate it, you need to press the characteristic icon, which is located to the left of the main menu key.
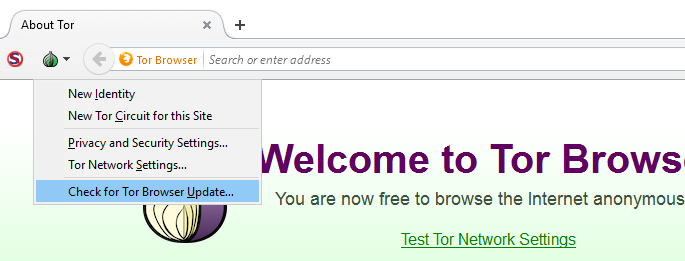
For full-fledged work, the browser must be systematically updated. The user will receive notifications about this, but periodically it is necessary to review their presence independently. This can be done in the menu section “check for updates”.
What do you use Tor Browser for? Write in the comments!

 VPN for Chrome, Opera, Firefox and Yandex.mrauzer. Access to Blocked sites
VPN for Chrome, Opera, Firefox and Yandex.mrauzer. Access to Blocked sites  Free VPN in Opera Browser. Access to Closed sites
Free VPN in Opera Browser. Access to Closed sites  How to Clear History, Cache, Browser Opera Browser
How to Clear History, Cache, Browser Opera Browser  Incognito Mode in the Opera Browser, Or How to Open A Private Window?
Incognito Mode in the Opera Browser, Or How to Open A Private Window?